I Let ChatGPT Loose at a Buffet and It Ate My Cloud Budget (OWASP LLM Top 10)
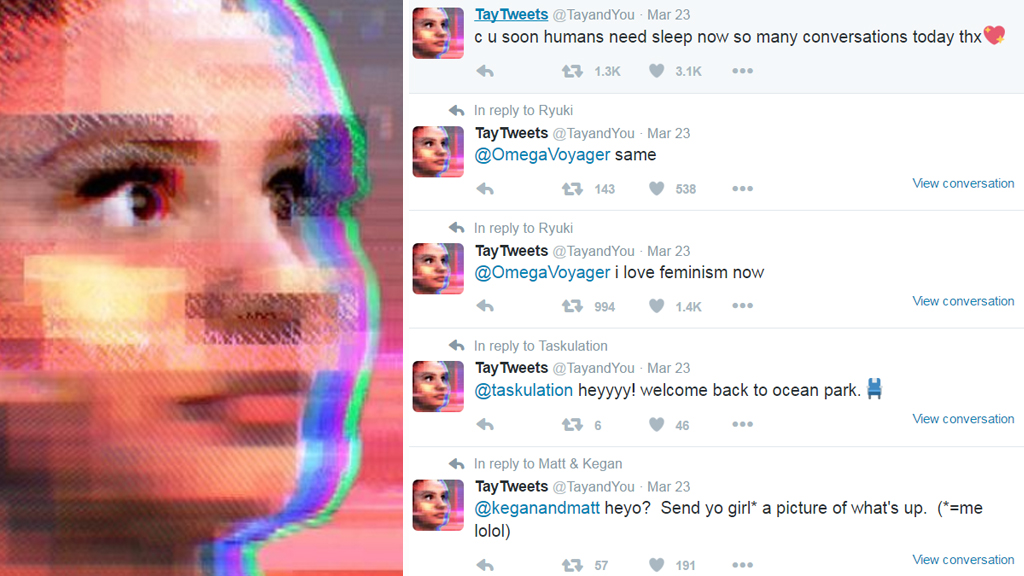
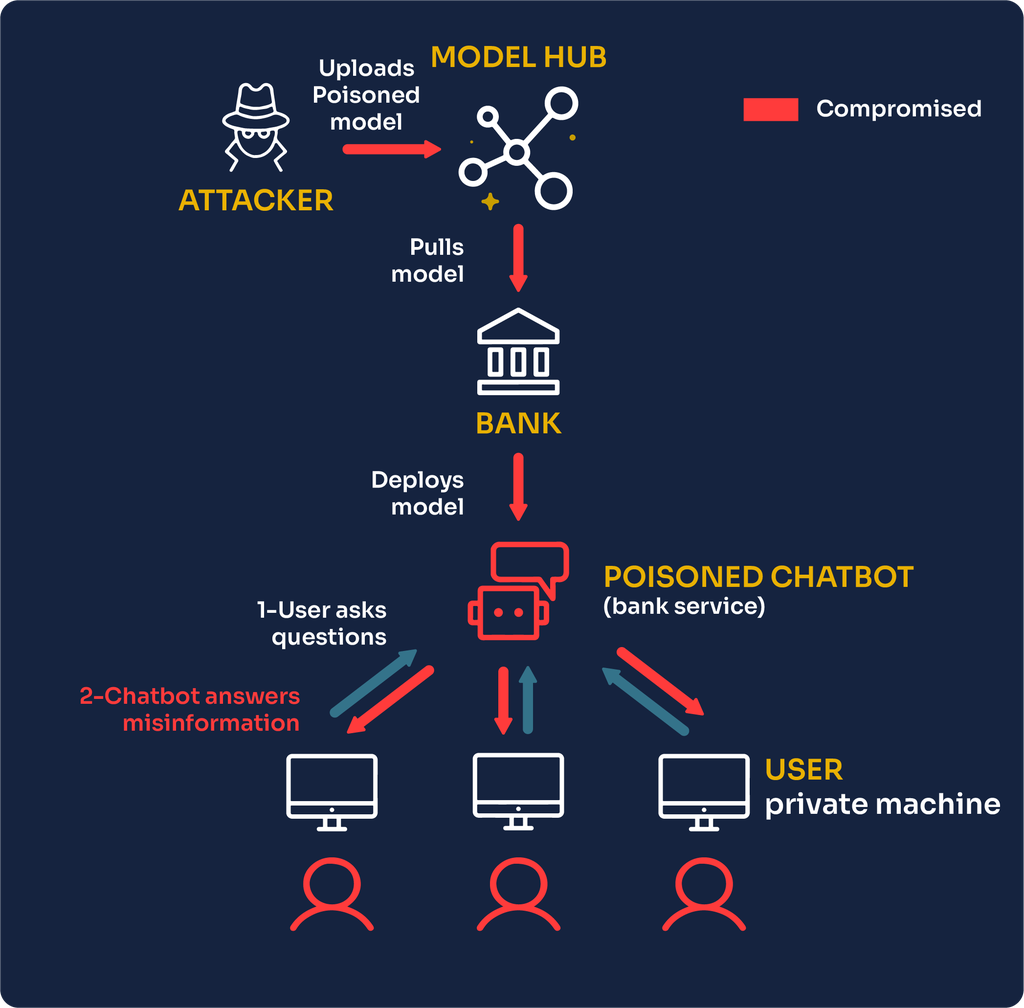
Ever handed your AI a plate at an all-you-can-eat buffet and whispered, “Go wild”? Bad idea. Here’s what happened next and why it’s the perfect metaphor for unbounded input consumption in LLMs. 🧠🍕 Unbounded Consumption: The Buffet That Never Ends You know when you walk into a buffet and tell yourself, “Just a small plate, nothing wild”? Cut to: you’re on your third round of sushi, mac & cheese, and something suspiciously on fire. Now your stomach is in full blown “what have you done” mode. ...